Globally, the value of payment fraud in 2019 was $28.65 billion. In the EU/SEPA region, the total value of fraudulent card transactions was estimated at €1.87 billion in the same year. In an increasingly digital world, where consumers shop, e-bank, work, date, take out insurance and pay using a growing number of local and global payment methods, fraudsters are also becoming more inventive. In 2020, e-commerce has grown – certainly under the influence of lockdowns by COVID-19 – and with it the number of relatively anonymous Card-Not-Present (CNP) transactions has increased exponentially. CNP transactions are a Valhalla for financial criminals. CNP transactions accounted for €1.50 Billion of the total card fraud losses, 80% of all card fraud.
Card fraud has been at the top of financial crime statistics for years. New payment methods offer criminals new opportunities to scam companies or rob consumers by using their ID. Outsiders can make use of corrupt, internal employees who leak information and give the fraudster access to sensitive data. Skimming, Phishing, ID theft rob customers and threaten the reputation and financial stability of financial service providers. Risk management departments must identify, assess and prevent new risks by implementing new protocols and work processes, and staff must be trained to recognise suspicious activities. The responsibility of the board is to drive processes that minimise risk through a proactive risk management strategy.
What types of risk are we talking about?
- financial risk;
- damage to reputation;
- money laundering;
- fraud;
- non-compliance;
- cyber attacks;
- other forms of risk.
Legislators targeted banks, mortgage lenders, insurers and other financial service providers. As more and more payments moved online and e-commerce grew enormously, Payment Service Providers (PSP) and Merchant Acquirers – companies that handle digital payments – were forced to invest in compliance and risk management to meet regulatory requirements and help prevent financial crime. Especially as regulators and supervisors received signals that digital payments made money tracking more difficult and turned into a money launderer’s paradise. Companies that have enthusiastically entered the crypto-currency market since the Bitcoin craze have not been spared. These companies are forced to invest an increasing amount of their budgets in risk management to prevent fraud and other forms of financial crime.
Independent of the type, risk management consists of several elements:
- awareness of the potential risks;
- identification;
- evaluation;
- risk management/control;
- implementation of protocols;
- monitoring of risks.
Risk monitoring is an ongoing process, in which risks are periodically evaluated and weighed, allowing risk protocols to be improved, thanks to newly acquired knowledge. This is a crucial part of the risk management process, because criminals are constantly adapting their modus operandi to new technology and they discover loopholes, which they skilfully exploit.
Managing and adapting manual procedures requires well-trained staff. This can be done much more quickly and accurately. Innovative technologies have changed the financial market forever (Fintech) and are now also transforming the compliance and risk management departments of financial institutions through Regtech solutions that support, complement or replace these complex manual processes. This allows financial service providers to focus on their core business: providing financial services.
Regtech solutions translate structured and unstructured data into so-called decision rules that help to detect and prevent risks in time. Regtech helps to optimise work processes and make risk manageable by adapting and, where necessary, changing procedures. Risks can be monitored, as Regtech ‘sounds the alarm’ when it detects unusual patterns.
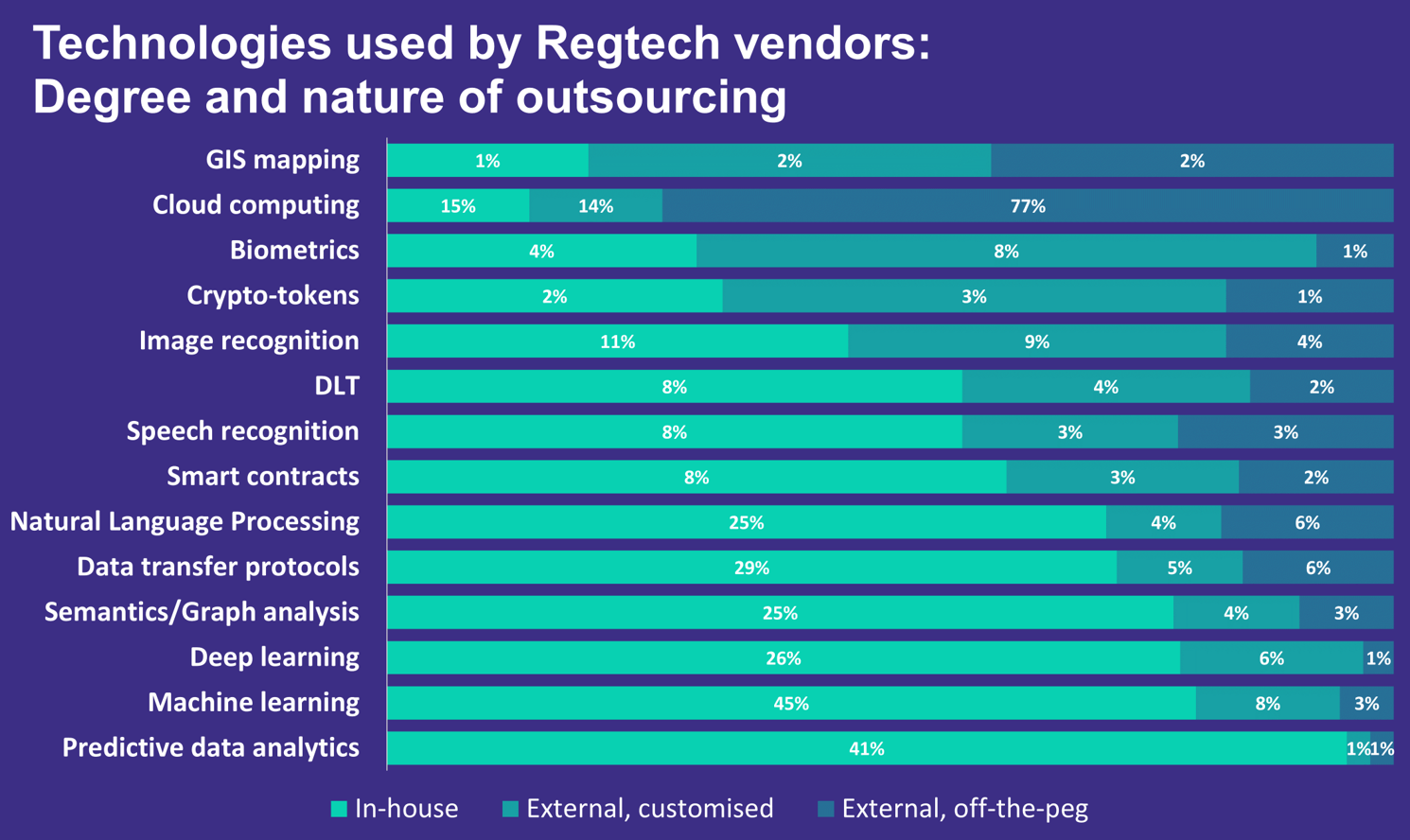
Regtech provides companies with a multitude of innovative cloud-based solutions that detect financial crime in a timely manner by analysing available data and detecting unusual patterns in time using a wide range of innovative technologies. The table below from a report by the Cambridge Center of Alternative Finance shows which innovative technologies are most commonly used by Regtech companies to help financial institutions automate and optimise risk management processes.
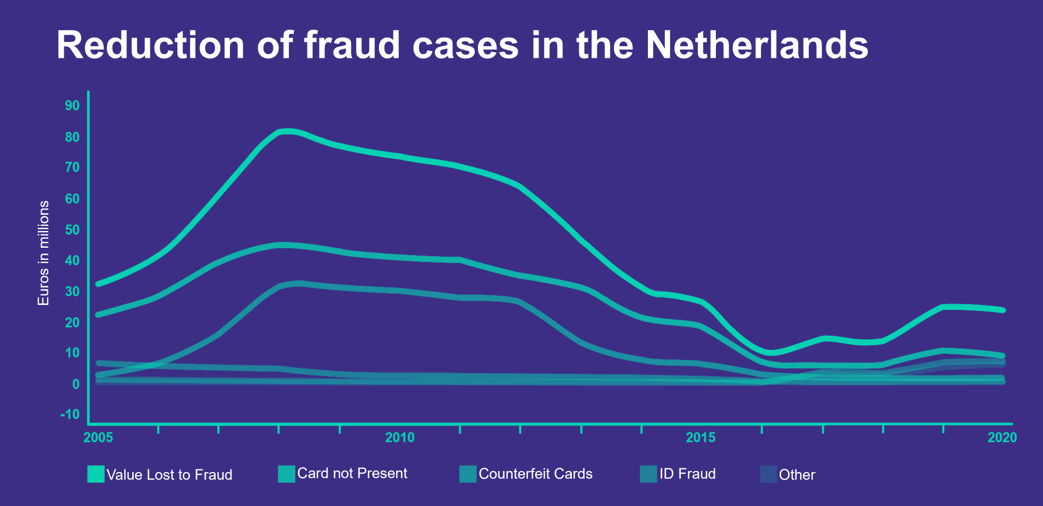
The Netherlands is doing remarkably well compared to other countries in the EU. Early adoption of 3D-Secure, the DigiD, Geo-Blocking of debit cards and a relatively low use of credit cards through the immensely popular IDEAL, have particularly helped to slow down credit card fraud, which has grown explosively in other countries.
Nevertheless, more and more Dutch service providers are also seeing opportunities to optimise their risk management processes and procedures through integration with powerful Regtech solutions. Hyarchis has been a market leader in document and data management for decades, and in recent years has focused on offering Regtech solutions to financial service providers.
Would you like information about the risk management solutions that Hyarchis can offer your organization? Please contact us without obligation via the button below:





